Decryption of files and text
This time, I will explain how to decrypt the encrypted text data.
📄️ Cryptence of files and text
It is assumed that it will work not only on on -premises software but also with cloud services.There are some actions related to security and encryption.Explains how to encrypt text files.
📄️ Calculation of hash values
This section describes how to have a hash of text and file data and calculate the hash value.
encryption technology and precautions
This time, we use AES encryption technology.
It is still a technology that is still used in many environments, and is also used to connect with WiFi router and terminal.
It is difficult to analyze at a brute force, and if the key length is set to 256 bits, analysis is said to take several hundred trillion years.
It is classified into a common key code, and requires the same password for decay and decryptation.
Therefore, if thepassword is lost, the data will not be able to decrypt to the original state.
If you use Power Automate Desktop with AES, be sure to refrain from password for decrypt.
In addition, as I will explain the method of decoding this time, it is very difficult to analyze at the braid hit as mentioned above.
Even if you forget your password, you know the encryption algorithm, and if the number of digits in the password is small, you may be able to decod the number of digits is not very realistic.
Please note that the explanation is limited to cases in which the encrypted data using Power Automate Desktop using the same password.
How to set the password
As mentioned above, a password is required to encrypt and decrypt it using AES.
The password specification can be set flexibly, such as direct input and input using variables, but the recommendation is the input variable marked as confidential information.
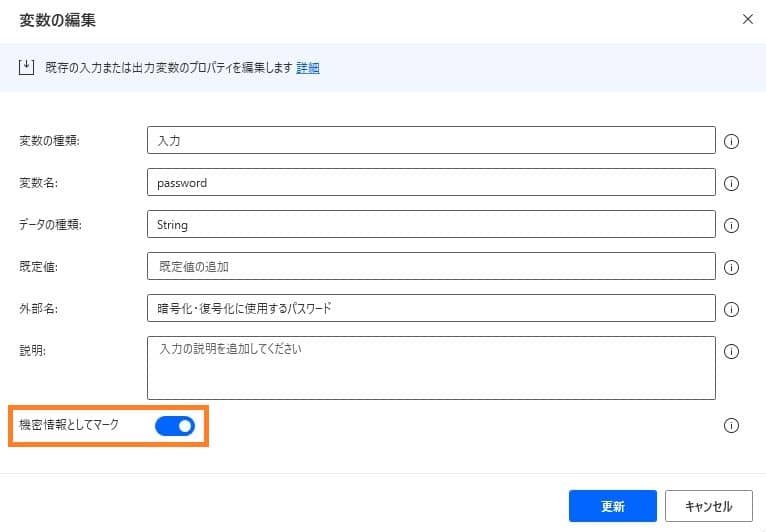
With this method, you can keep your password safely, even when setting or execution.
To decrypt specific text data
Use an action called "Decoding text with AES" when decrypt certain string information that has already been encrypted.
Details of action "Dissonating text with AES" action
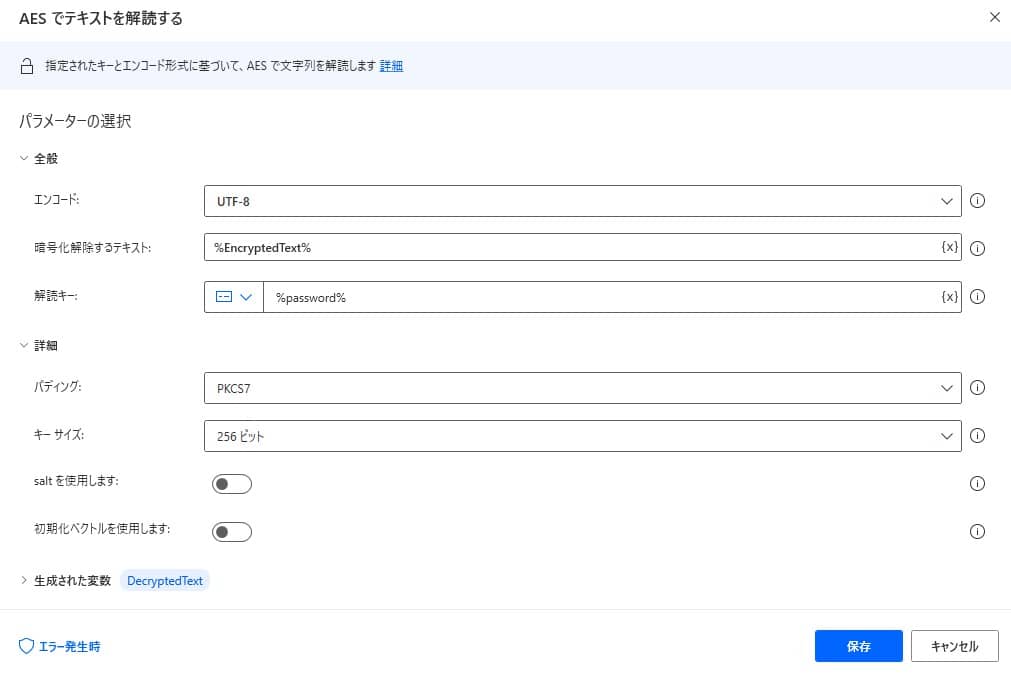
The action has the following parameters.
| Parameter name | value |
|---|---|
| Encoding | Character string for the character string to be created |
| Text to decrypt | Target text to decrypt |
| Decryption key | Password used for decoding |
Implement a sample flow with copy and paste
As a sample, we have prepared a flow that encrypts the text data once and decrypt it using the same key.
Copy the following code and paste it on the edit screen of Power Automate Desktop to add the target action.
The password assumes that there is an input variable named "Password" in the above -mentioned method.
SET TargetString TO $'''%'Target text to be encrypted'%'''
Cryptography.EncryptText.EncryptTextWithAES Encoding: Cryptography.EncryptionEncoding.UTF8 TextToEncrypt: TargetString EncryptionKey: password PaddingMode: Cryptography.PaddingMode.PKCS7 KeySize: Cryptography.AESKeySize.Bits256 EncryptedText=> EncryptedText
Cryptography.DecryptText.DecryptTextWithAES Encoding: Cryptography.EncryptionEncoding.UTF8 TextToDecrypt: EncryptedText DecryptionKey: password Padding: Cryptography.PaddingMode.PKCS7 KeySize: Cryptography.AESKeySize.Bits256 DecryptedText=> DecryptedText
When you execute it, you can check that the target data is encrypted, and the decrypt result and the target data match.
Operate and implement Power Automate Desktop
From "Search for action", enter "Dissonating text with AES".
Set the parameter as follows
Parameter name value Encoding UTF-8 Text to decrypt %"Text data to be decrypted"% Decryption key Password used for decoding By execution, the specified string is decoded using AES.
Exceptions that can occur
If the decryption setting is not appropriate or contains unsupported character strings, an error may occur during the decryption.
We recommend that you implement block processing.